OPC UA Security Best Practices: A Complete Guide to Securing Industrial IoT Communications
- eclatron tech
- Dec 11, 2025
- 25 min read
Introduction: Why OPC UA Security Matters in Industrial IoT

Industrial automation systems face unprecedented cybersecurity challenges in 2025. As manufacturing facilities, energy plants, and industrial operations across Germany embrace digital transformation, securing machine-to-machine communication has become critical. OPC Unified Architecture (OPC UA) serves as the backbone of industrial IoT communications, connecting programmable logic controllers (PLCs), supervisory control and data acquisition (SCADA) systems, and manufacturing execution systems (MES) across production environments.
The convergence of information technology (IT) and operational technology (OT) introduces significant security vulnerabilities. According to recent cybersecurity threat intelligence reports, industrial control systems experienced a 140% increase in cyberattacks targeting critical infrastructure. For German manufacturers navigating Industry 4.0 transformation, implementing robust OPC UA security measures protects intellectual property, ensures operational continuity, and maintains regulatory compliance with IEC 62443 standards and NIS2 Directive requirements.
This comprehensive guide explores OPC UA security best practices, covering authentication mechanisms, encryption protocols, network segmentation strategies, vulnerability management, and compliance frameworks essential for securing industrial automation networks.
Understanding OPC UA Security Architecture Fundamentals
What is OPC UA and Why Security is Critical
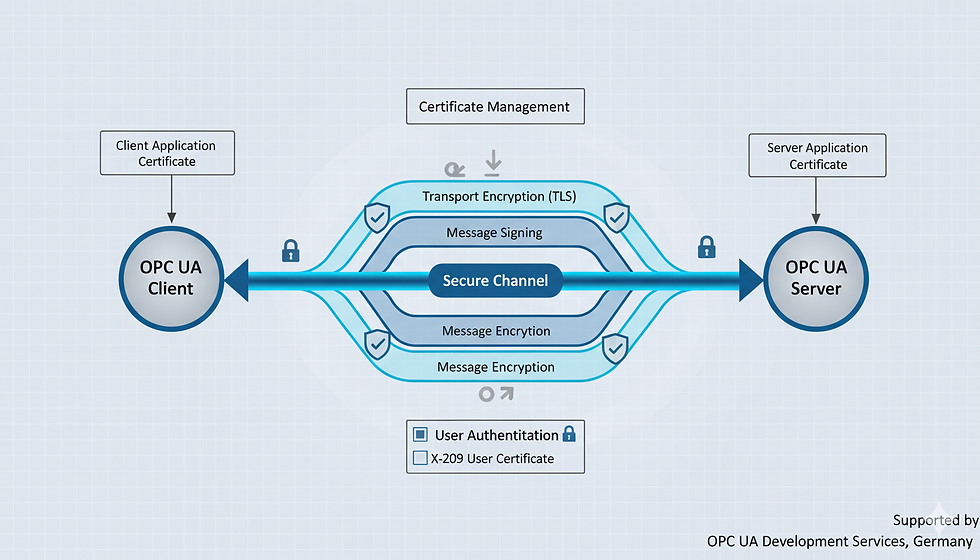
OPC Unified Architecture represents a platform-independent service-oriented architecture developed by the OPC Foundation for secure, reliable industrial data exchange. Unlike legacy OPC Classic protocols that relied on Windows DCOM technology, OPC UA integrates security by design with built-in encryption, authentication, and authorization mechanisms.
The security model addresses three fundamental pillars:
Confidentiality: Protecting sensitive industrial data through encryption prevents unauthorized access to production parameters, proprietary processes, and operational metrics. Manufacturing facilities handling confidential product specifications require end-to-end data protection.
Integrity: Data integrity verification ensures that information transmitted between OPC UA clients and servers remains unaltered. Tampered sensor readings or modified control commands could cause production disruptions, safety incidents, or quality defects.
Availability: Ensuring continuous operation of industrial communication infrastructure prevents downtime costs averaging €220,000 per hour in automotive manufacturing sectors. Denial-of-service attacks targeting OPC UA servers can halt entire production lines.
OPC UA Security Architecture Components
The OPC UA security framework incorporates multiple defense layers:
Application Instance Certificates: X.509 digital certificates uniquely identify OPC UA applications, enabling mutual authentication between clients and servers. Certificate-based authentication prevents unauthorized devices from connecting to industrial networks.
Security Policies: Configurable security policies define cryptographic algorithms for encryption and signing. OPC UA supports multiple security policies including Basic256Sha256, Aes128_Sha256_RsaOaep, and Aes256_Sha256_RsaPss, allowing organizations to balance security strength with performance requirements.
Security Modes: Three security modes provide flexibility:
None: No encryption or signing (only for isolated test environments)
Sign: Message signing ensures integrity without encryption overhead
SignAndEncrypt: Maximum security with both signing and encryption
User Authentication: Multiple authentication methods support diverse industrial scenarios:
Username/password authentication
X.509 user certificates
Kerberos / Active Directory (GSSAPI) Authentication
Token-Based Authentication (OAuth2 / JWT)
Authorization Model: Role-based access control (RBAC) restricts users to specific operations based on organizational roles, implementing least-privilege principles across industrial automation systems.
Critical OPC UA Security Threats in Industrial Environments
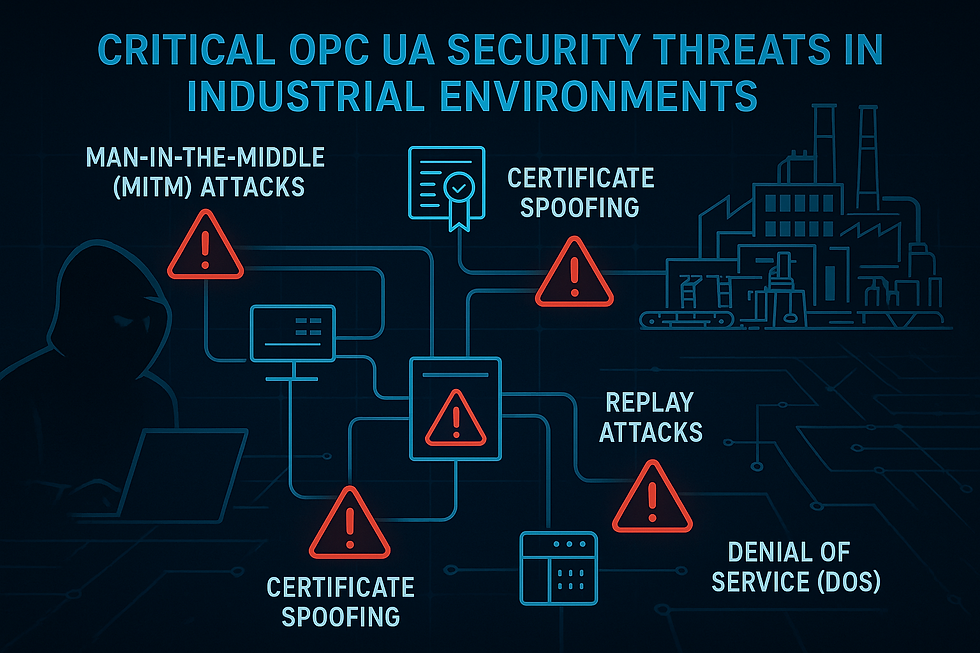
Common Attack Vectors Targeting Industrial Protocols
Understanding threat landscapes helps prioritize security investments:
Man-in-the-Middle (MITM) Attacks: Adversaries intercepting unencrypted OPC UA communications can steal sensitive process data or inject malicious commands. Manufacturing environments using OPC UA without encryption expose production secrets and enable process manipulation.
Certificate Spoofing: Improperly validated certificates allow attackers to impersonate legitimate OPC UA servers or clients, gaining unauthorized access to industrial control systems. Certificate trust chain verification prevents spoofing attacks.
Replay Attacks: Captured legitimate OPC UA messages replayed at later times can trigger unintended operations. Timestamp validation and sequence numbering defend against replay attack scenarios.
Denial of Service (DoS): Resource exhaustion attacks targeting OPC UA servers disrupt industrial communications, causing production stoppages. Rate limiting, connection throttling, and resource monitoring mitigate DoS risks.
Credential Theft: Weak authentication mechanisms or stolen credentials provide attackers persistent access to industrial networks. Multi-factor authentication and hardware security modules protect authentication credentials.
Firmware Vulnerabilities: Unpatched OPC UA implementations contain exploitable security flaws. The 2022 OPC UA vulnerability (CVE-2022-29865) affecting multiple vendors demonstrated importance of timely security updates.
Insider Threats: Authorized personnel with excessive privileges pose risks through intentional sabotage or unintentional errors. Comprehensive audit logging and access reviews detect anomalous behaviors.
Real-World Industrial Cybersecurity Incidents
Recent incidents underscore OPC UA security importance:
The Oldsmar water treatment facility attack in 2021 exploited weak remote access controls, demonstrating critical infrastructure vulnerability. Although not specifically OPC UA-related, the incident highlighted industrial protocol security gaps.
German automotive suppliers experienced targeted attacks exploiting unencrypted industrial communications to steal manufacturing process intellectual property. These incidents accelerated adoption of encrypted OPC UA implementations across automotive supply chains.
Ransomware campaigns like WannaCry and NotPetya disrupted global manufacturing operations, affecting German industrial facilities using legacy systems without proper network segmentation. Modern OPC UA security architectures implement defense-in-depth strategies preventing lateral movement.
Source : URL: https://commercial.allianz.com/news-and-insights/expert-risk-articles/cyber-attacks-on-critical-infrastructure.html
Implementing Strong OPC UA Authentication Mechanisms
Certificate-Based Authentication Best Practices
X.509 certificates form the foundation of OPC UA authentication:
Certificate Generation and Management:
Generate unique certificates for each OPC UA application instance
Use minimum 2048-bit RSA keys (4096-bit recommended for critical systems)
Implement proper certificate hierarchies with root and intermediate CAs
Set appropriate certificate validity periods (12-24 months for application certificates)
Include accurate subject alternative names (SANs) for proper identity verification
Certificate Trust Establishment:
Maintain separate trusted and rejected certificate stores
Implement manual certificate approval workflows for production environments
Avoid automatic certificate acceptance in operational systems
Regularly review and prune certificate trust stores
Document certificate trust decisions for audit compliance
Certificate Renewal Processes:
Establish automated certificate renewal procedures before expiration
Plan certificate rotation schedules minimizing operational disruption
Maintain certificate inventory tracking expiration dates
Test certificate renewal procedures in development environments
Implement certificate expiration monitoring and alerting
Private Key Protection:
Store private keys in hardware security modules (HSMs) for critical systems
Use filesystem permissions restricting key access to authorized processes
Encrypt private keys at rest with strong passphrases
Implement key backup and recovery procedures
Never transmit private keys over networks
User Authentication Strategy Development
Complement application authentication with robust user authentication:
Username/Password Authentication Hardening:
Enforce strong password policies (minimum 12 characters, complexity requirements)
Implement account lockout after failed authentication attempts
Use password hashing with salt (never store plaintext passwords)
Enable multi-factor authentication where supported
Rotate passwords according to organizational security policies
Certificate-Based User Authentication:
Issue user certificates from trusted certificate authorities
Bind certificates to specific user identities
Store user certificates on smart cards or USB tokens
Implement certificate revocation checking
Audit all certificate-based authentication events
Enterprise Authentication Integration:
Integrate OPC UA with Active Directory or LDAP directories
Implement Kerberos authentication for Windows environments
Synchronize user provisioning and deprovisioning processes (User provisioning and deprovisioning synchronization ensures that when employees join, change roles, or leave an organization, their access credentials across all OPC UA systems are automatically updated in real-time, preventing security gaps from orphaned accounts or delayed access removal that could enable unauthorized system access.)
Configuring OPC UA Encryption and Data Protection
Selecting Appropriate Security Policies
Choose security policies matching threat models:
Basic256Sha256: Provides strong security with broad compatibility. Suitable for most industrial applications requiring confidentiality and integrity protection. Uses RSA-2048 encryption and SHA-256 hashing.
Aes128_Sha256_RsaOaep: Modern security policy offering better performance than Basic256Sha256 while maintaining strong security. Recommended for new OPC UA deployments with supported devices.
Aes256_Sha256_RsaPss: Maximum security strength for highly sensitive applications handling critical infrastructure controls or valuable intellectual property. Performance impact requires evaluation on resource-constrained devices.
Security Policy Selection Criteria:
Assess computational capabilities of OPC UA endpoints
Evaluate data sensitivity and classification levels
Consider regulatory compliance requirements (IEC 62443, NIS2)
Balance security strength with system performance requirements
Verify security policy support across all OPC UA components
Implementing End-to-End Encryption
Comprehensive encryption strategies protect data across communication paths:
Transport Layer Security:
Enable OPC UA SecureChannel providing message-level encryption
Configure appropriate security modes (Sign or SignAndEncrypt)
Validate security mode enforcement across all connections
Monitor for security mode downgrades indicating potential attacks
Implement secure renegotiation preventing MITM attacks
Application-Level Encryption:
Encrypt sensitive data fields within OPC UA messages
Protect credentials and secrets using additional encryption layers
Implement data masking for non-production environments
Use field-level encryption for regulatory compliance requirements
Consider performance implications of multiple encryption layers
Network Layer Protection:
Deploy virtual private networks (VPNs) for remote OPC UA access
Implement IPsec for network-level encryption when required
Use encrypted tunnels for OPC UA traffic crossing untrusted networks
Configure firewall rules restricting OPC UA port access (4840/4843)
Segment industrial networks isolating OPC UA communications
Network Segmentation and OPC UA Security Zones
Implementing Industrial Network Architecture
Proper network segmentation limits attack surface and contains breaches:
Purdue Model Implementation: The Purdue Enterprise Reference Architecture provides framework for industrial network segmentation:
Level 0 (Physical Process): Sensors, actuators, physical equipment Level 1 (Basic Control): PLCs, DCS controllers, RTUs Level 2 (Supervisory Control): HMI, SCADA systems, OPC UA servers Level 3 (Manufacturing Operations): MES, batch management systems Level 4 (Business Planning): ERP, enterprise resource planning Level 5 (Enterprise Network): Corporate IT infrastructure
OPC UA Deployment Considerations:
Deploy OPC UA servers at Level 2 serving supervisory control functions
Position OPC UA clients at Level 3 for manufacturing operations data access
Implement data diodes for one-way data flows from OT to IT
Use OPC UA aggregating servers for data consolidation at demilitarized zones (DMZ)
Restrict direct connectivity between Level 1-2 and Level 4-5
Firewall Rules and Access Control Lists
Configure precise firewall rules governing OPC UA traffic:
Inbound Rules:
Allow OPC UA discovery endpoint access (port 4840) only from authorized subnets
Permit OPC UA secure channel connections (port 4843) with source IP whitelisting
Block OPC UA ports from internet-facing interfaces
Implement stateful inspection for OPC UA connection establishment
Log all firewall rule matches for security monitoring
Outbound Rules:
Restrict OPC UA client connections to approved server IP addresses
Block unauthorized OPC UA client applications using application whitelisting
Monitor for unexpected outbound OPC UA connections indicating compromise
Implement egress filtering preventing data exfiltration
Document all approved OPC UA communication paths
DMZ Architecture:
Position OPC UA aggregating servers in industrial DMZ
Implement dual firewalls creating screened subnet
Use proxy servers mediating OPC UA connections between zones
Deploy intrusion detection systems (IDS) monitoring DMZ traffic
Maintain separate security monitoring for DMZ components
Industrial Protocol Gateway Security
OPC UA gateways bridging legacy protocols require special attention:
Gateway Hardening:
Deploy gateways on dedicated hardened servers
Minimize installed software to essential functions only
Implement host-based intrusion prevention systems (HIPS)
Enable comprehensive logging for gateway operations
Regularly update gateway firmware and security patches
Protocol Translation Security:
Validate data during protocol conversion preventing injection attacks
Implement rate limiting on legacy protocol sides
Monitor for protocol anomalies indicating exploitation attempts
Use separate credentials for OPC UA and legacy protocol sides
Audit gateway configuration changes
OPC UA Vulnerability Management and Patch Procedures
Vulnerability Assessment Strategies
Proactive vulnerability identification reduces exploitation risks:
OPC UA Stack Vulnerability Scanning:
Inventory all OPC UA implementations including versions and vendors
Subscribe to OPC Foundation security advisories and vulnerability disclosures
Monitor CVE databases for OPC UA-related vulnerabilities
Use industrial protocol scanners identifying OPC UA security weaknesses
Conduct annual penetration testing focusing on OPC UA implementations
Security Testing Methodologies:
Perform fuzzing tests on OPC UA endpoints discovering parsing vulnerabilities
Conduct certificate validation testing ensuring proper trust chain verification
Test authentication mechanisms for bypass vulnerabilities
Verify encryption implementation correctness using protocol analyzers
Evaluate DoS resilience through stress testing
Third-Party Component Assessment:
Audit OPC UA software dependencies for known vulnerabilities
Review open-source OPC UA stacks for security issues
Evaluate proprietary OPC UA implementations through vendor security documentation
Request vendor security certifications and independent audit reports
Participate in information sharing and analysis centers (ISACs)
Patch Management for Industrial Control Systems
Applying security updates requires careful planning in production environments:
Change Management Process:
Establish formal change approval procedures for OPC UA updates
Document baseline configurations before applying patches
Perform risk assessments evaluating patch deployment risks
Create rollback procedures enabling rapid recovery if issues occur
Communicate planned maintenance windows to stakeholders
Testing and Validation:
Deploy patches in development environments mirroring production
Conduct functional testing verifying OPC UA communication integrity
Perform regression testing ensuring patches don't introduce issues
Validate security improvements through post-patch scanning
Document test results and obtain approval before production deployment
Deployment Strategies:
Prioritize critical security patches addressing actively exploited vulnerabilities
Use phased rollout approaches deploying patches to pilot systems first
Schedule maintenance windows during planned downtime periods
Implement automated patch deployment for non-critical systems where possible
Maintain patch inventory tracking deployment status across OPC UA infrastructure
Compensating Controls: When immediate patching isn't feasible:
Implement network-level protections blocking exploitation attempts
Enhance monitoring detecting exploitation activities
Restrict access to vulnerable OPC UA endpoints
Deploy virtual patching through intrusion prevention systems
Document risk acceptance and compensating control effectiveness
Monitoring and Logging OPC UA Security Events
Comprehensive Security Event Logging
Visibility into OPC UA operations enables threat detection:
Essential Logging Categories:
Authentication Events:
Successful and failed authentication attempts with timestamps
User identity information and source IP addresses
Authentication method used (certificate, username/password)
Certificate validation results and trust decisions
Session establishment and termination events
Authorization Events:
Access attempts to restricted OPC UA nodes
Permission denied events with requested operations
Role changes and privilege escalations
Administrative actions and configuration modifications
Audit log tampering attempts
Communication Events:
Security policy and mode negotiation results
Secure channel establishment and renewal
Unexpected connection attempts from unknown sources
Security mode downgrades or policy changes
Protocol errors and malformed messages
Operational Events:
OPC UA server start/stop events
Certificate expiration warnings and renewals
Configuration changes to security settings
Performance anomalies indicating DoS attacks
Resource exhaustion events and error conditions
Security Information and Event Management Integration
Centralize OPC UA logs for correlation and analysis:
SIEM Integration Best Practices:
Forward OPC UA logs to SIEM platforms using syslog or log collectors
Normalize OPC UA log formats for consistent parsing
Enrich logs with contextual information (asset inventory, user directories)
Create correlation rules detecting multi-stage attacks
Integrate OPC UA logs with IT security events for comprehensive visibility
Alerting and Response:
Configure real-time alerts for critical security events
Implement escalation procedures for security incidents
Define runbooks for common OPC UA security scenarios
Integrate with security orchestration and automated response (SOAR) platforms
Establish metrics measuring mean time to detect (MTTD) and respond (MTTR)
Log Retention and Compliance:
Retain OPC UA logs meeting regulatory requirements (typically 1-7 years)
Implement tamper-proof log storage preventing deletion or modification
Encrypt archived logs protecting sensitive operational information
Establish log backup and recovery procedures
Conduct periodic log reviews identifying security trends
OPC UA Compliance and Regulatory Requirements
IEC 62443 Industrial Cybersecurity Standard
IEC 62443 provides comprehensive framework for industrial automation security:
Relevant IEC 62443 Parts for OPC UA:
IEC 62443-3-3: System security requirements defining security levels (SL) 1-4
SL 1: Protection against casual or coincidental violation
SL 2: Protection against intentional violation using simple means
SL 3: Protection against intentional violation using sophisticated means
SL 4: Protection against intentional violation using sophisticated means with extended resources
IEC 62443-4-2: Component security requirements applicable to OPC UA implementations
Security capability levels defining security functions
Requirements for authentication, encryption, integrity, and availability
Secure development lifecycle requirements for OPC UA products
Implementing IEC 62443 Compliance:
Conduct security risk assessments identifying required security levels
Map OPC UA security features to IEC 62443 foundational requirements
Document security architecture meeting zone and conduit requirements
Implement defense-in-depth strategies spanning multiple security layers
Maintain security documentation for compliance audits
NIS2 Directive and Critical Infrastructure Protection
The updated Network and Information Security (NIS2) Directive strengthens EU cybersecurity requirements:
NIS2 Applicability:
Essential entities: Energy, transport, healthcare, digital infrastructure
Important entities: Manufacturing, food production, chemical industry
German implementation through IT-Sicherheitsgesetz 2.0 Source : https://eur-lex.europa.eu/eli/dir/2022/2555/oj
OPC UA Security Requirements Under NIS2:
Risk management measures appropriate to threats and vulnerabilities
Business continuity including backup and disaster recovery
Supply chain security considering OPC UA component providers
Security in network and information systems including OPC UA infrastructure
Incident handling and reporting within 24-72 hours
Cryptography and encryption protecting sensitive data
Compliance Demonstration:
Maintain OPC UA security documentation and risk assessments
Implement incident response plans addressing OPC UA security events
Conduct regular security audits and penetration testing
Report significant OPC UA security incidents to authorities
Demonstrate continuous improvement of security measures
GDPR Considerations for Industrial IoT Data
General Data Protection Regulation applies when OPC UA transmits personal data:
GDPR Relevance to OPC UA: Industrial data may contain personal information:
Operator login credentials and authentication logs
Maintenance technician activity records
Production worker performance metrics
Video surveillance integrated with industrial systems
Privacy-by-Design Principles:
Minimize personal data collection in OPC UA implementations
Implement pseudonymization and anonymization techniques
Encrypt personal data at rest and in transit
Establish data retention periods and automated deletion
Document legal basis for processing industrial personal data Source: According to the EU NIS2 Directive (Directive (EU) 2022/2555), organizations operating critical infrastructure must implement risk management measures, maintain business continuity capabilities, and report significant cybersecurity incidents within 24-72 hours. 1.https://www2.deloitte.com/content/dam/Deloitte/lu/Documents/risk/lu-nis2-directive-guide.pdf 2.https://eur-lex.europa.eu/eli/dir/2022/2555/oj 3.https://digital-strategy.ec.europa.eu/en/policies/nis2-directive 4.https://www.enisa.europa.eu/topics/cybersecurity-policy/nis-directive-new 5.URL: https://www.bsi.bund.de/EN/Topics/Regulation/IT-Security-Act/it-security-act_node.html 6.URL: https://www2.deloitte.com/content/dam/Deloitte/lu/Documents/risk/lu-nis2-directive-guide.pdf 7.https://www.cisa.gov/topics/cyber-threats-and-advisories/information-sharing/eu-nis2-directive
OPC UA Security Best Practices Implementation Roadmap
Phase 1: Security Assessment and Planning (Weeks 1-4)
Baseline Assessment:
Inventory all OPC UA implementations across industrial infrastructure
Document current security configurations and policies
Identify security gaps and vulnerabilities
Assess compliance with IEC 62443 and NIS2 requirements
Prioritize security improvements based on risk
Security Strategy Development:
Define target security architecture and security levels
Establish security policies and standards for OPC UA deployments
Create implementation roadmap with timelines and responsibilities
Allocate budget and resources for security improvements
Obtain management approval and stakeholder buy-in
Phase 2: Foundation Security Controls (Weeks 5-12)
Quick Wins:
Enable SignAndEncrypt security mode on all OPC UA connections
Implement strong authentication mechanisms replacing default credentials
Deploy certificate-based authentication for critical systems
Configure firewall rules restricting OPC UA port access
Enable comprehensive logging for security events
Network Segmentation:
Implement Purdue Model network architecture
Deploy firewalls between OPC UA zones
Configure access control lists limiting communication paths
Establish DMZ for OPC UA aggregating servers
Deploy intrusion detection systems monitoring OPC UA traffic
Phase 3: Advanced Security Hardening (Weeks 13-24)
Certificate Infrastructure:
Deploy certificate authority for OPC UA certificate management
Implement automated certificate renewal procedures
Establish certificate trust governance and approval workflows
Deploy hardware security modules for critical private keys
Create certificate inventory and expiration tracking
Monitoring and Response:
Integrate OPC UA logs with SIEM platform
Configure security event alerting and escalation
Establish security operations center (SOC) procedures for OPC UA incidents
Conduct tabletop exercises simulating OPC UA security incidents
Measure and optimize security monitoring effectiveness
Phase 4: Continuous Improvement (Ongoing)
Vulnerability Management:
Subscribe to OPC UA security advisories and vulnerability feeds
Conduct quarterly vulnerability assessments
Implement patch management procedures
Perform annual penetration testing
Participate in threat intelligence sharing communities
Compliance Maintenance:
Conduct annual IEC 62443 gap assessments
Maintain NIS2 compliance documentation
Perform regular security audits
Update security policies reflecting evolving threats
Train personnel on OPC UA security best practices
Advanced OPC UA Security Topics
Secure OPC UA Client Development
Developers building OPC UA clients must implement security correctly:
Client Security Requirements:
Validate server certificates against trusted certificate stores
Never accept invalid or untrusted certificates automatically
Implement secure credential storage for authentication
Use appropriate security policies and modes
Handle security errors gracefully without compromising safety
Secure Coding Practices:
Input validation preventing injection attacks
Output encoding preventing cross-site scripting in web-based HMIs
Secure session management and timeout handling
Protection against buffer overflows and memory corruption
Regular security code reviews and static analysis
OPC UA PubSub Security Considerations
OPC UA Publisher-Subscriber model introduces unique security requirements:
Message-Level Security:
Encrypt and sign PubSub messages protecting multicast communications
Use group security keys distributed to authorized subscribers
Implement key rotation preventing compromised key exploitation
Protect against message replay using sequence numbers
Validate message integrity before processing
Access Control:
Authenticate publishers preventing unauthorized data injection
Authorize subscribers ensuring only approved receivers access data
Implement topic-based access control restricting message visibility
Monitor for unauthorized publication or subscription attempts
Audit PubSub configuration changes
OPC UA Cloud Connectivity Security
Connecting OPC UA to cloud platforms requires additional security:
Edge Gateway Hardening:
Deploy OPC UA edge gateways with minimal attack surface
Implement mutual TLS authentication for cloud connections
Use IoT device identity certificates for gateway authentication
Enable edge data filtering and aggregation reducing cloud data exposure
Implement offline operation capabilities maintaining resilience
Cloud Security Controls:
Use cloud provider identity and access management (IAM)
Implement network segmentation for cloud-connected OPC UA services
Enable cloud security logging and monitoring
Encrypt data at rest in cloud storage
Conduct cloud security assessments and compliance audits
Troubleshooting Common OPC UA Security Issues
Certificate-Related Problems
Issue: Client cannot connect due to certificate validation failure Solution:
Verify certificate validity periods (not expired or not yet valid)
Check certificate trust store includes server certificate or root CA
Validate certificate subject alternative names match server hostname
Ensure certificate hasn't been revoked
Review certificate chain completeness
Issue: "Bad_SecurityChecksFailed" error during connection Solution:
Verify matching security policy and mode on client and server
Check certificate private key accessibility
Validate certificate and private key pairing
Ensure adequate entropy for cryptographic operations
Review security audit logs for specific failure reasons
Authentication and Authorization Failures
Issue: User authentication fails with valid credentials Solution:
Verify username/password entered correctly
Check user account status (locked, disabled, expired)
Validate user exists in authentication backend
Review authentication method compatibility
Check for time synchronization issues affecting Kerberos
Issue: Access denied when reading/writing OPC UA nodes Solution:
Verify user role assignments and permissions
Check node-level access control configuration
Validate role-based access control rules
Review audit logs identifying specific authorization failure
Confirm user session establishment completed successfully
Performance Issues with Encryption
Issue: Significant performance degradation after enabling encryption Solution:
Evaluate hardware capabilities supporting cryptographic operations
Consider using Aes128 instead of Aes256 for better performance
Implement hardware cryptographic acceleration where available
Optimize subscription publishing intervals reducing encryption overhead
Use Sign mode instead of SignAndEncrypt for non-sensitive data
Conclusion: Building Resilient OPC UA Security Architecture
Securing OPC UA communications requires comprehensive approach spanning technology, processes, and people. German industrial organizations implementing these best practices achieve:
Threat Resilience: Multi-layered defenses protecting against evolving cyber threats Regulatory Compliance: Meeting IEC 62443, NIS2, and GDPR requirements Operational Continuity: Preventing security incidents disrupting production Competitive Advantage: Protecting intellectual property and maintaining customer trust
Successful OPC UA security implementation follows defense-in-depth principles:
Strong authentication and encryption as foundation
Network segmentation limiting attack surface
Continuous monitoring detecting threats early
Regular vulnerability management maintaining security posture
Compliance verification demonstrating due diligence
As Industry 4.0 adoption accelerates across German manufacturing, energy, and critical infrastructure sectors, OPC UA security becomes business imperative rather than technical concern. Organizations partnering with experienced OPC UA service providers accelerate security maturity while focusing on core business objectives.
The journey toward comprehensive OPC UA security requires sustained commitment, but payoffs include operational resilience, regulatory compliance, and protection of valuable industrial assets driving digital transformation success.
AEO Optimization: Top 20 "Also Searches" Questions with Semantic Answers
1. What is OPC UA security and why is it important?
OPC UA security refers to the comprehensive cybersecurity framework built into the OPC Unified Architecture protocol protecting industrial automation communications. It encompasses authentication mechanisms verifying device and user identities, encryption protocols ensuring data confidentiality, integrity verification preventing message tampering, and authorization controls restricting access based on roles. Security is critical because industrial control systems face increasing cyber threats targeting critical infrastructure, manufacturing facilities, and energy systems. OPC UA security protects against unauthorized access, data theft, production disruptions, safety incidents, and regulatory non-compliance while enabling secure Industry 4.0 digital transformation initiatives.
2. How does OPC UA encryption work?
OPC UA encryption operates through secure channel protocol establishing encrypted communication sessions between clients and servers. During connection establishment, endpoints negotiate security policies defining cryptographic algorithms (such as AES-128 or AES-256 for symmetric encryption and RSA for asymmetric encryption). The protocol uses X.509 certificates for key exchange, generating session-specific symmetric keys encrypting message payloads. OPC UA supports multiple security modes: None (no encryption), Sign (message signing for integrity), and SignAndEncrypt (full encryption and signing). Modern implementations use AES-GCM (Galois/Counter Mode) in Publish/Subscribe (PubSub) providing authenticated encryption ensuring both confidentiality and integrity in single cryptographic operation, protecting industrial data from interception and tampering during transmission across networks.
3. What are OPC UA certificates and how do they work?
OPC UA certificates are X.509 digital certificates uniquely identifying OPC UA applications and users, enabling mutual authentication between communicating parties. Application instance certificates identify specific OPC UA servers and clients, while user certificates authenticate individuals accessing industrial systems. Certificates contain public keys, identity information (subject name, organization), validity periods, and digital signatures from issuing certificate authorities. During OPC UA connection establishment, endpoints exchange certificates, validate trust chains against configured certificate stores (trusted, rejected, issuer lists), verify validity periods and signatures, then use certificate public keys for asymmetric encryption establishing secure channels. Proper certificate management including generation, distribution, validation, renewal, and revocation forms the foundation of OPC UA security architecture.
4. What is the difference between OPC UA security modes?
OPC UA defines three security modes providing different protection levels: None mode provides no encryption or signing, transmitting data in plaintext suitable only for isolated test environments or air-gapped networks without security requirements. Sign mode applies digital signatures to messages ensuring integrity and authenticity without encrypting payload data, useful when computational overhead is concerned but data confidentiality isn't required. SignAndEncrypt mode provides maximum security applying both digital signatures and encryption protecting confidentiality, integrity, and authenticity simultaneously, recommended for production industrial environments handling sensitive operational data. Organizations should use SignAndEncrypt mode for all production OPC UA deployments unless specific performance constraints necessitate Sign mode after thorough risk assessment.
5. How to implement OPC UA authentication?
Implementing OPC UA authentication requires configuring multiple security layers:
Application Authentication uses X.509 certificates uniquely identifying OPC UA clients and servers, implemented by generating certificates for each application instance, establishing trust relationships through certificate stores, and enforcing mutual authentication during connection establishment.
User Authentication verifies individual identities through username/password combinations (strengthened with complexity requirements and MFA), X.509 user certificates (stored on smart cards or hardware tokens), Kerberos tickets (integrated with Windows Active Directory), or Token-Based Authentication (OAuth2 / JWT). Best practices include disabling anonymous authentication in production, implementing strong password policies, using certificate-based authentication for critical systems, integrating with enterprise identity management systems, enforcing multi-factor authentication where supported, and comprehensively logging all authentication events for security monitoring and compliance.
6. What are OPC UA security policies?
OPC UA security policies define specific cryptographic algorithms and security mechanisms used for securing communications between clients and servers. Common security policies include
Basic256Sha256 (RSA-2048 encryption, AES-256-CBC symmetric encryption, HMAC-SHA-256 signing),
Aes128_Sha256_RsaOaep (RSA-OAEP key transport, AES-128-CBC encryption, HMAC-SHA-256 signing), and
Aes256_Sha256_RsaPss (RSA-PSS signatures, AES-256-CBC encryption, SHA-256 hashing). Policies balance security strength against computational overhead, with stronger policies providing better protection but requiring more processing power. Organizations select policies based on threat models, hardware capabilities, regulatory requirements, and performance constraints. Modern OPC UA deployments should use Basic256Sha256 minimum, with Aes256_Sha256_RsaPss for highly sensitive critical infrastructure applications requiring maximum security protection.
7. How to troubleshoot OPC UA security issues?
Troubleshooting OPC UA security issues requires systematic diagnostic approach:
Certificate Problems - verify certificate validity periods, check trust store configuration, validate certificate chains, confirm subject alternative names match hostnames, and review certificate revocation status.
Authentication Failures - confirm correct credentials, check user account status, verify authentication method compatibility, ensure time synchronization for Kerberos, and review authentication backend connectivity.
Connection Errors - validate matching security policies and modes, verify firewall rules allow OPC UA ports (4840, 4843), check network connectivity, confirm endpoint URLs accuracy, and review server security configuration.
Performance Issues - evaluate hardware cryptographic capabilities, optimize security policy selection, adjust subscription parameters reducing encryption overhead, and monitor resource utilization. Always review OPC UA stack logs, security audit trails, and use protocol analyzers like Wireshark with OPC UA dissector for detailed message inspection identifying root causes.
8. What is IEC 62443 and how does it relate to OPC UA?
IEC 62443 is an international standard series defining cybersecurity requirements for industrial automation and control systems, providing a comprehensive framework for securing industrial environments including OPC UA implementations. The standard defines security levels (SL 1-4) indicating protection sophistication, foundational requirements covering identification and authentication, use control, data integrity, data confidentiality, restricted data flow, and timely response to events. IEC 62443-3-3 specifies system-level security requirements including network segmentation and security zones applicable to OPC UA architectures. IEC 62443-4-2 defines component-level requirements directly applicable to OPC UA products and implementations. Organizations achieve IEC 62443 compliance by mapping OPC UA security features to standard requirements, implementing appropriate security levels based on risk assessments, documenting security architectures, and maintaining security throughout system lifecycle including procurement, design, implementation, operation, and maintenance phases.
9. How to secure OPC UA connections over the internet?
Securing OPC UA connections over the internet requires multiple defense layers: VPN Tunneling - establish encrypted VPN tunnels (IPsec or SSL VPN) creating secure channels for OPC UA traffic traversing public networks. OPC UA Security - enable SignAndEncrypt security mode with strong security policies (Aes256_Sha256_RsaPss), implement certificate-based authentication preventing unauthorized access, and validate certificates against properly managed trust stores. Network Architecture - deploy OPC UA servers behind firewalls with port forwarding or reverse proxies, use DMZ architecture isolating internet-facing components, implement intrusion detection/prevention systems monitoring traffic, and restrict access through IP whitelisting. Access Control - implement VPN authentication requiring multi-factor authentication, use client certificates for device authentication, maintain least-privilege access principles, and regularly review remote access permissions. Monitoring - comprehensively log all remote OPC UA connections, alert on anomalous access patterns, and integrate with SIEM for correlation with other security events.
10. What are common OPC UA vulnerabilities?
Common OPC UA vulnerabilities include
Certificate Validation Weaknesses - improper certificate chain verification allowing spoofed certificates, inadequate certificate revocation checking enabling compromised certificate use, and automatic certificate acceptance creating trust management gaps.
Authentication Bypasses - weak default credentials (admin/admin), anonymous authentication enabled in production, and insufficient session timeout enforcement.
Encryption Implementation Flaws - downgrade attacks forcing weaker security policies, improper random number generation weakening cryptography, and CBC mode padding oracle vulnerabilities.
Denial of Service - resource exhaustion through excessive connection attempts, buffer overflows in message parsing, and XML entity expansion attacks.
Memory Safety Issues - buffer overflows in C/C++ OPC UA stacks, use-after-free vulnerabilities, and integer overflows. Regular vulnerability scanning, timely patching, secure configuration management, and defense-in-depth architecture mitigate these risks effectively protecting OPC UA implementations from exploitation attempts.
11. How to implement OPC UA network segmentation?
Implementing OPC UA network segmentation follows Purdue Enterprise Reference Architecture organizing industrial networks into security zones:
Level 0-1 (Process and Control) - deploy PLCs and field devices on isolated networks with no direct OPC UA access from upper levels.
Level 2 (Supervisory) - position OPC UA servers providing data to manufacturing operations, protected by firewalls from Level 3.
Level 3 (Operations) - place OPC UA clients accessing manufacturing data, separated from corporate networks.
DMZ Architecture - deploy OPC UA aggregating servers in demilitarized zones mediating communications between zones, with dual firewalls providing defense-in-depth.
Firewall Configuration - create explicit access control lists permitting only required OPC UA communications, block OPC UA ports (4840, 4843) at zone boundaries except approved paths, implement stateful inspection, and log all zone crossings.
Data Diodes - use unidirectional gateways for sensitive applications requiring one-way data flow from OT to IT preventing reverse access completely.
12. What is OPC UA GDS (Global Discovery Server)?
OPC UA Global Discovery Server (GDS) provides centralized certificate management for large-scale OPC UA deployments, automating certificate lifecycle including issuance, renewal, and revocation. GDS acts as certificate authority issuing application instance certificates and user certificates to OPC UA applications, maintains certificate revocation lists (CRLs) enabling validation of compromised certificates, and provides discovery services helping clients locate OPC UA servers across networks. Benefits include Automated Certificate Management reducing manual administration overhead, Consistent Security Policies enforced across all registered applications, Simplified
Trust Management through centralized trust store distribution, and Scalability supporting thousands of OPC UA endpoints efficiently. GDS implementation requires Secure Infrastructure protecting GDS private keys using hardware security modules, Access Control restricting certificate issuance to authorized applications, Audit Logging tracking all certificate operations, and High Availability ensuring continuous certificate services availability for production systems.
13. How does OPC UA compare to MQTT security?
OPC UA and MQTT implement security differently reflecting their design purposes: OPC UA Security provides comprehensive built-in security with certificate-based mutual authentication, multiple security policies offering strong encryption, application-level security independent of transport, role-based access control, and session-level security. MQTT Security relies primarily on transport layer security (TLS) for encryption, supports username/password authentication, and requires additional layers for authorization and encryption at application level. Key Differences - OPC UA integrates security as core architectural component while MQTT security depends on external mechanisms, OPC UA provides message-level security surviving network transport changes while MQTT protects connection-level only, OPC UA offers granular node-level access control while MQTT has topic-based permissions. For industrial automation, OPC UA's integrated security architecture provides better protection, though MQTT+TLS suffices for less critical IoT applications. Many deployments use both protocols with OPC UA for critical control communications and MQTT for telemetry data collection.
14. What are OPC UA user roles and permissions?
OPC UA implements role-based access control (RBAC) restricting users to operations matching their organizational responsibilities. Common roles include
Administrator - full access including security configuration, user management, and system administration;
Operator - read/write access to operational variables enabling process control; Maintenance - access to diagnostic information and maintenance functions;
Engineer - configuration privileges for system setup and commissioning;
Observer - read-only access for monitoring without control capabilities; and
Auditor - access to logs and audit trails without operational permissions. Permissions define allowed operations:
Read (viewing variable values),
Write (modifying variables), Execute (invoking methods),
Browse (discovering node structure),
HistoryRead (accessing historical data), and
Subscribe (receiving data change notifications). Organizations implement least-privilege principles assigning minimum permissions necessary for job functions, regularly review user access rights detecting privilege creep, enforce separation of duties preventing single-person critical operations, and comprehensively audit all permission changes maintaining accountability and compliance.
15. How to monitor OPC UA security events?
Monitoring OPC UA security events requires a comprehensive logging strategy:
Essential Events - authentication successes/failures with user identity and source IP, authorization denials with requested operations, security policy negotiations and changes, certificate validation results and trust decisions, session establishments/terminations, secure channel creations, and administrative configuration changes.
Logging Infrastructure - enable OPC UA audit logging at highest verbosity capturing security-relevant events, forward logs to centralized SIEM platform using syslog or log collectors, normalize OPC UA log formats for consistent parsing, enrich logs with asset inventory and user directory context, and implement secure log storage preventing tampering.
Alerting - configure real-time alerts for critical events (repeated authentication failures, certificate validation failures, security mode downgrades, unauthorized access attempts), establish escalation procedures for security incidents, and integrate with security operations center (SOC) workflows.
Analysis - create correlation rules detecting multi-stage attacks, establish baselines identifying anomalous behaviors, generate security metrics measuring MTTD and MTTR, and conduct periodic log reviews identifying security trends requiring attention.
16. What is the NIS2 Directive and how does it affect OPC UA?
NIS2 (Network and Information Security Directive 2) is updated EU cybersecurity legislation strengthening security requirements for critical infrastructure and important sectors. Effective across EU member states including Germany, NIS2 mandates
Risk Management implementing appropriate technical and organizational measures including OPC UA security controls,
Incident Reporting notifying authorities of significant security incidents within 24-72 hours,
Supply Chain Security assessing cybersecurity risks from OPC UA component vendors, Business Continuity maintaining backup and disaster recovery for industrial communications, and
Governance establishing cybersecurity policies and accountability.
OPC UA Implications - organizations must implement strong authentication and encryption, conduct regular OPC UA vulnerability assessments and penetration testing, maintain comprehensive security documentation, report OPC UA security incidents meeting significance thresholds, and demonstrate continuous security improvement. German implementation through IT-Sicherheitsgesetz 2.0 adds specific requirements for critical infrastructure operators. Non-compliance risks significant penalties up to €10 million or 2% of global revenue, plus personal liability for management.
17. How to implement OPC UA certificate management?
Implementing robust OPC UA certificate management requires structured approach: Certificate Generation - create unique certificates for each OPC UA application instance using minimum 2048-bit RSA keys (4096-bit for critical systems), include accurate subject information and subject alternative names, and set appropriate validity periods (12-24 months).
Certificate Authority - establish internal CA for issuing OPC UA certificates or use trusted third-party CA, implement proper CA key protection using hardware security modules, maintain certificate revocation lists (CRLs), and document certificate issuance policies.
Trust Management - maintain separate certificate stores (trusted, rejected, issuer certificates), implement manual certificate approval workflows for production systems, regularly review and prune certificate trust stores, and document trust decisions for audit compliance.
Renewal Automation - establish certificate inventory tracking expiration dates, implement automated renewal procedures before expiration, plan renewal schedules minimizing operational disruption, and enable certificate expiration alerting.
Revocation Handling - immediately revoke compromised certificates, distribute updated CRLs to all OPC UA endpoints, remove revoked certificates from trust stores, and audit revocation effectiveness.
18. What are OPC UA security best practices for SCADA systems?
Securing OPC UA in SCADA environments requires comprehensive approach: Network Isolation - deploy SCADA networks physically or logically separated from corporate IT, implement firewall rules restricting OPC UA communications to approved paths, use unidirectional gateways for data historian connections, and eliminate direct internet connectivity to SCADA OPC UA servers. Strong Authentication - implement certificate-based authentication for all SCADA OPC UA communications, eliminate default and shared credentials, integrate with enterprise identity management, and enforce multi-factor authentication for remote access. Encryption - enable SignAndEncrypt security mode with strong policies (Basic256Sha256 minimum), encrypt data at rest in SCADA historians, and protect backup data through encryption. Access Control - implement role-based access control restricting operators to authorized SCADA functions, enforce principle of least privilege, regularly review user permissions, and maintain separation of duties. Monitoring - comprehensively log all SCADA OPC UA operations, integrate logs with SIEM for correlation, alert on security anomalies, and establish incident response procedures. Resilience - implement redundant OPC UA servers for availability, maintain offline operation capabilities, and test disaster recovery procedures regularly.
19. How to perform OPC UA penetration testing?
OPC UA penetration testing evaluates security posture through controlled exploitation attempts: Pre-Engagement - define scope including OPC UA endpoints, establish rules of engagement preventing production disruption, obtain authorization documentation, and plan testing during maintenance windows. Information Gathering - discover OPC UA servers through port scanning (4840, 4843), enumerate supported security policies and modes, identify OPC UA stack implementations and versions, and map network architecture. Vulnerability Scanning - use specialized OPC UA security scanners, test for known CVEs affecting identified OPC UA stacks, check certificate validation weaknesses, and identify authentication bypass vulnerabilities. Exploitation - attempt certificate spoofing attacks, test for authentication weaknesses, evaluate encryption implementation correctness, conduct denial-of-service testing, and attempt privilege escalation. Post-Exploitation - assess lateral movement possibilities, evaluate data exfiltration risks, and test incident detection capabilities. Reporting - document discovered vulnerabilities with CVSS scores, provide remediation recommendations prioritized by risk, and present findings to stakeholders with executive summary. Engage qualified industrial cybersecurity professionals experienced with OT environments preventing unintended safety or production impacts.
20. What is the future of OPC UA security?
OPC UA security evolves addressing emerging threats and technological advances: Post-Quantum Cryptography - OPC Foundation is evaluating quantum-resistant cryptographic algorithms to ensure that OPC UA communication remains secure in a future where quantum computers may compromise current encryption methods. Zero Trust Architecture - increasingly adopting continuous verification, micro-segmentation, and least-privilege access regardless of network location. AI-Powered Threat Detection - machine learning algorithms analyzing OPC UA traffic patterns detecting sophisticated attacks and anomalies invisible to signature-based systems. Blockchain for Integrity - Technologies such as distributed ledgers and blockchain are being explored for providing immutable audit trails in critical industrial operations, offering stronger guarantees of data integrity. Enhanced Authentication - OPC UA systems are expected to integrate with modern identity providers that support biometric authentication, behavioral analytics, multi-factor authentication, and hardware-based identity — strengthening security beyond traditional passwords or certificates. Cloud-Native Security - securing OPC UA in containerized, microservices architectures with service mesh security, secrets management, and cloud-native certificate authorities. Automated Security - Future OPC UA ecosystems may include self-healing security mechanisms capable of automatically responding to intrusions, performing automated patching, and optimizing configurations with AI-assisted tools. Organizations preparing for these trends invest in flexible security architectures accommodating new technologies while maintaining operational resilience and regulatory compliance throughout digital transformation journeys.




Comments